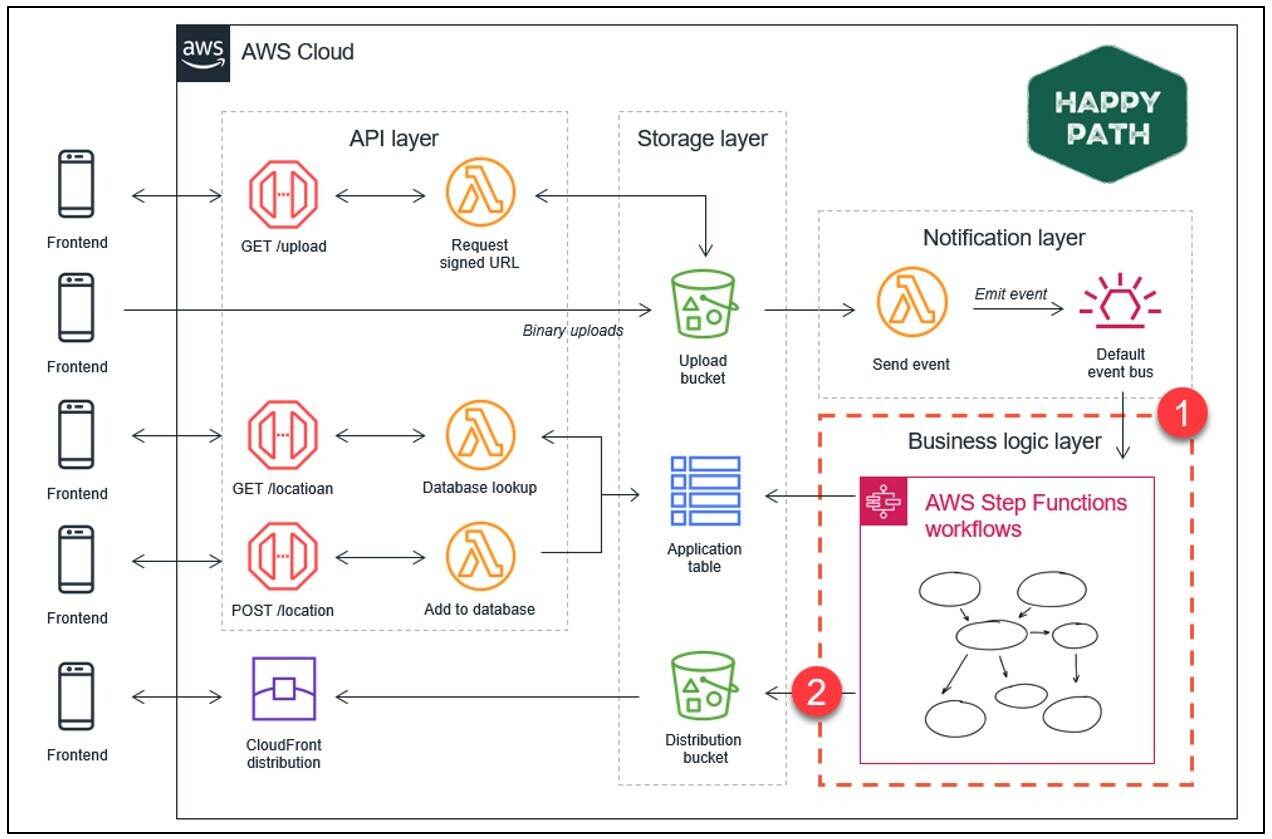
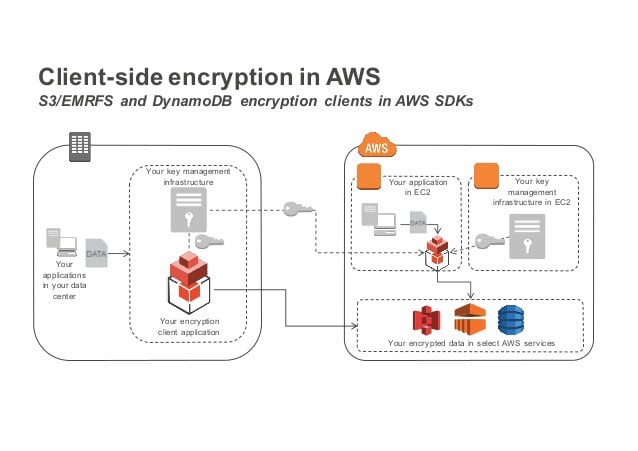
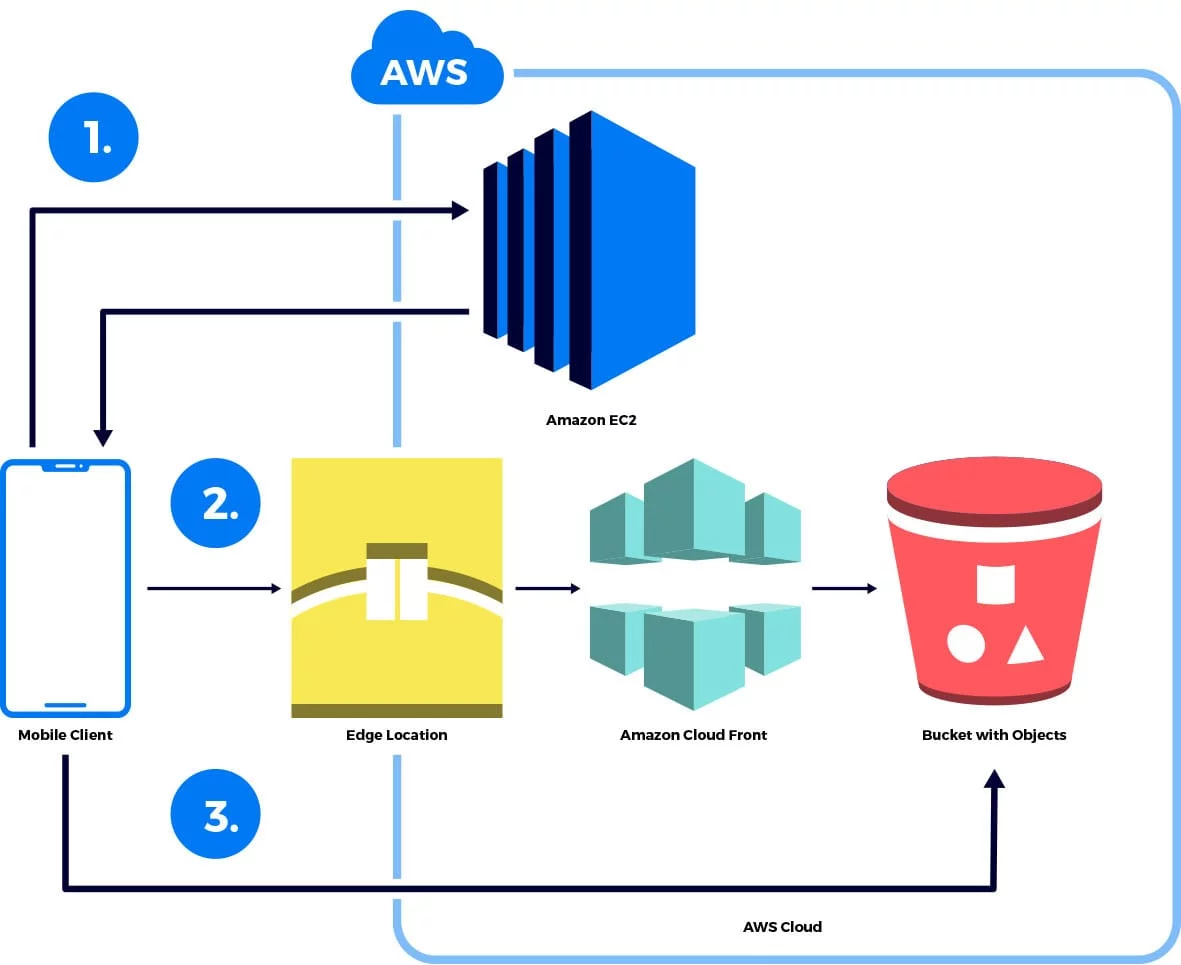
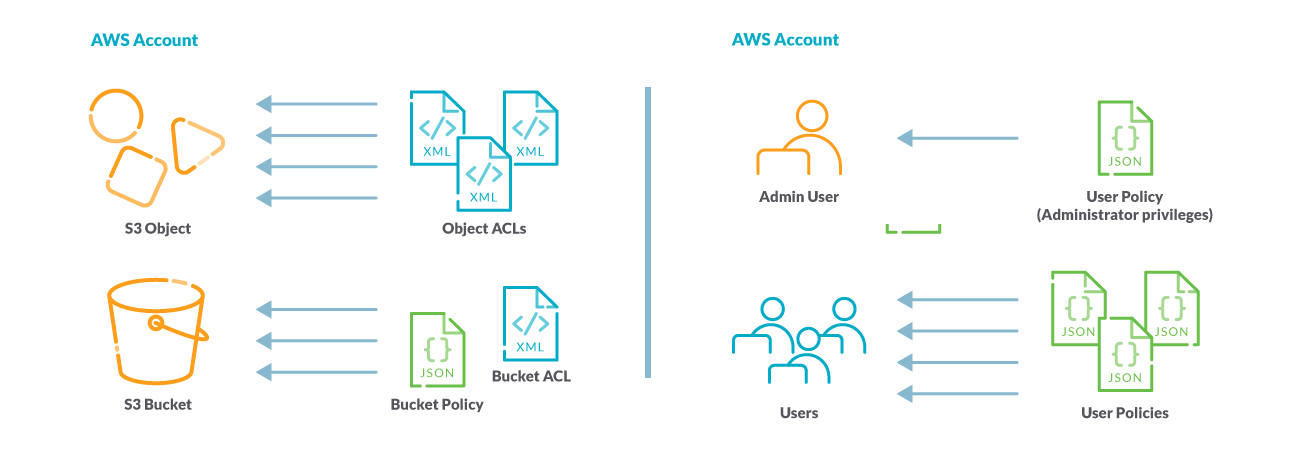
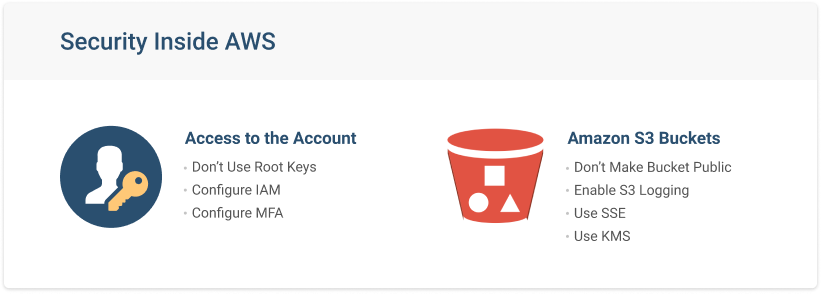
How to Use Bucket Policies and Apply Defense-in-Depth to Help Secure Your Amazon S3 Data | AWS Security Blog
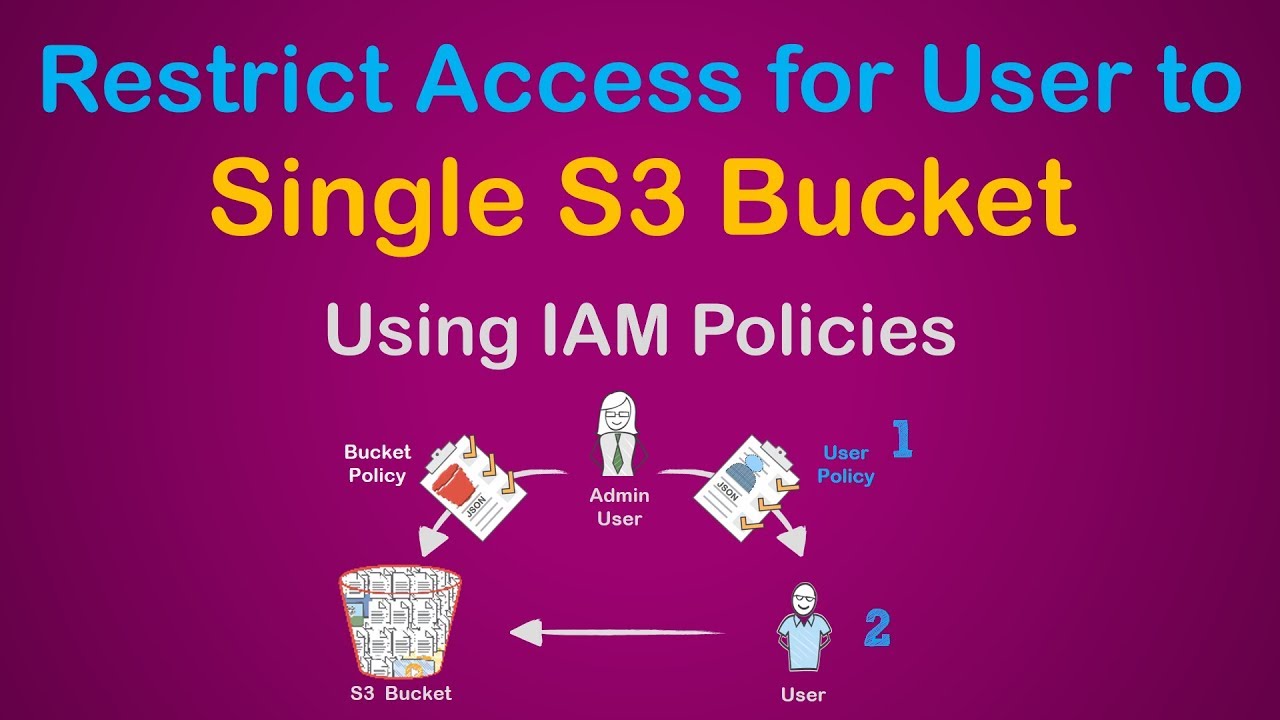
AWS S3 Bucket Security 👮- Restrict Privileges🔒to User using IAM Policy | Grant User Access - YouTube

How to scale your authorization needs by using attribute-based access control with S3 | AWS Security Blog

Amazon S3 Malware Scanning Using Trend Micro Cloud One and AWS Security Hub | AWS Partner Network (APN) Blog